PlugX is able to communicate with a command and Command (C2) server once the contaminated Laptop or computer connects to the net.
We are now observing destructive attackers targeting people with a wave of ‘MFA fatigue attacks,’ the place they bombard victims with MFA drive notifications – at an unprecedented fee – to trick them into authenticating their login tries.
Pretty much all the clubs and teams are non-gain corporations. Membership is generally open to the public and several demand a membership cost. Consider the next topics: Art, Crafts & Music Teams
MFA can help lower businesses’ attack surfaces by including Yet another layer of account protection. It dietary supplements the username and password product with A further factor only the user possesses, like their mobile phone.
Acquiring stolen bank card data is illegitimate and can result in severe lawful effects. Relying solely on platforms like Briansclub for protection can lead to complacency in utilizing appropriate cybersecurity protocols.
The movie's poster, featuring the 5 figures huddled alongside one another, was photographed by Annie Leibovitz towards the tip of capturing. The shot of five actors gazing within the digital camera affected the way in which teen films had been promoted from that point on.[eighteen]: 79–80, 325–326 The poster refers back to the 5 "varieties" of your story making use of somewhat distinctive phrases than All those Utilized in the film, and in another sequence, stating "They ended up 5 overall strangers with absolutely nothing in popular, meeting for The 1st time.
I'd do that sooner rather than afterwards mainly because I Actually don’t understand how it really works using your credit history report. If some other person is managing around creating buys with your name, I’d think that would have an affect on your credit rating score – nevertheless I'm not a hundred%.
Mod-Columbia Hoops can be an AAU league that offer basketball chances for athletes of all talents and talent concentrations. Our application allows us to work with athletes as young as 3rd grade via 12th grade.
[eleven] Hughes wrote the script around the time when he was producing Sixteen Candles, but he wrote the Sixteen Candles script in mere times and it impressed the studio executives and they selected it to be his directorial debut.[twelve]
Catwhisperer October 15, 2019 My bank (A serious a single during the US) has specifically recommended me not to implement PIN numbers and operate the debit card (with chip) like a charge card. Not many retailers power the PIN, and usually only at unmanned stations for instance self-checkout or perhaps the gas pump.
If two persons carry out an unlawful transaction and pay back cash. For the most part working with this simplistic case in point that transaction is untraceable. If those self same two people today perform an unlawful transaction and use bitcoin or similar copyright currencies that transaction IS traceable. You are able to figure out in which the brians club bitcoin came from, exactly where it's becoming sent to, and in the event the holders of your electronic wallets use that electronic wallet / forex Later on, Individuals transactions are traceable as well. It’s traceable from the beginning to the tip from the transaction. You are doing have some extent with some electronic assets such as (Monero, Z-dollars, Sprint, Lynda) who’s intent will be to obscure possession of your transaction.
But I realize that the banking institutions do not trouble tracking and prosecuting card fraud mainly because it’s less costly for them to simply think about it the expense of performing business enterprise. Perhaps therein lies the situation.
Get a great deal of stolen bank card knowledge from hackers and mark it on the market to fraudsters, who then use it for unlawful transactions or resale. Nevertheless primary, the marketplace method is effective very well.
The entire card details stolen from BriansClub was shared with various sources who function closely with economic institutions to detect and keep an eye on or reissue cards that clearly show up on the market in the cybercrime underground.
 Neve Campbell Then & Now!
Neve Campbell Then & Now!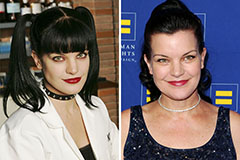 Pauley Perrette Then & Now!
Pauley Perrette Then & Now! Rachael Leigh Cook Then & Now!
Rachael Leigh Cook Then & Now! Jane Carrey Then & Now!
Jane Carrey Then & Now! Mike Smith Then & Now!
Mike Smith Then & Now!